Checkpoint Web Visualization Tool R71
EXPORT COMMANDS To download Rulebases50.fws & Objects50.C located in P1 to HTML C: cpwebview cpdb2html.bat C: cpwebview C: cpwebview -o.html To download the tools from the Checkpoint website, Extract the files to C: For R70 and above: The latest Web Visualization Tools are available in this new path Select which version you require R70 or R71 or R75 then look for Web Visualization Tool on last page of it, Extract the files to C: Note: The file will be a '.tgz', so to unzip you need tools like 7z or other supporting tools. To download 7z. PACKET INSPECTION/CAPTURE. fw monitor is able to capture packets at four different positions in the FireWall-1 chain: In contrast to other capturing tools like snoop or tcpdump, fw monitor does not use the promiscuous mode on network interface cards.
Pre-R80 Management Server Migration Tool. How to Check Point upgrade R77.30 to R80. R71 (aliases: R71_R71, 6.0.1.7) R75. Configuration Using the Web Interface. SecurePlatform enables easy configuration of your computer and networking setup, and the Check Point products installed on them. The Web Visualization tool is available at search for 'Web Visualization Tool' and filter. Is there any R71.
Based on the fact that FireWall-1 already receives all packets (due to the FireWall-1 kernel module between NIC driver and IP stack) fw monitor uses it’s own kernel module to capture packets (compared to filtering/encrypting them). Unlike snoop or tcpdump, fw monitor has the ability to capture packets at different positions in the FireWall-1 kernel module chain.
Snoop and tcpdump are capturing packets when they enter or leave the computer. Especially when NAT with FireWall-1 is involved fw monitor offers the possibility to capture packets at multiple locations (e.g. After the FireWall Virtual in inbound direction). This can help you to see how the packets are translated by the firewall and on which IP address the routing decission is made.

To see the firewall chain: fw ctl chain. SIMPLE TERMS. fw monitor grep (ip address) - It will provide the inspected packets of each interface. fw monitor grep (ip address) -o /tmp/monitor.cap - stores the output in /tmp folder with filename monitor.cap. Before the virtual machine in the inbound direction (i or PREIN).
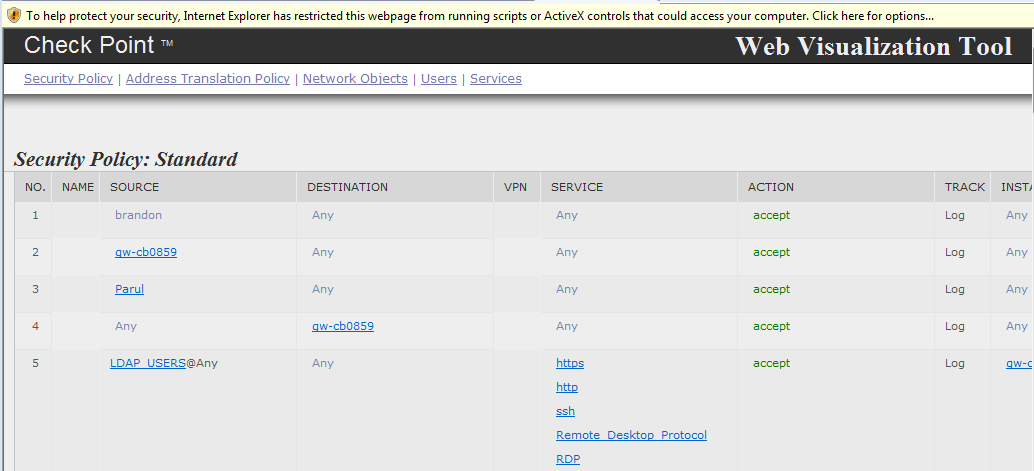
Check Point Web Visualization Tool
After the virtual machine in the inbound direction (I or POSTIN). Before the virtual machine in the outbound direction (o or PREOUT).
Checkpoint Web Visualization Tool
After the virtual machine in the outbound direction (O or POSTOUT) USING MACRO DEFINITIONS Use the below using fw monitor.e “accept src=10.102.104.5;” - To inspect packet for source ip address.